
#ReportersNotebook
You’ve likely heard the horror stories about weirdos hacking into baby monitors and whispering creepy messages to sleeping infants. In one recent case, a little boy tried to warn his parents about the “scary man in the monitor.”
Buzz Feed summarizes some of the creepiest hacks here:
7 Creepy Baby Monitor Stories That Will Terrify All Parents
However, a new study by the security research firm Rapid7 reveals that weirdos hacking your baby monitor to creep out your kid may be the least of your concerns.
In this white paper on baby monitor vulnerabilities, researchers explain “the Internet of things.” They point out that a hacker can target vulnerabilities in your baby monitor to access any device that is connected to your home Wi-Fi network.
This increases the risk of targeted attacks where crooks might even gain access to a company’s corporate server though an employee’s home computer—simply because that employee has a baby monitor in the home.
Corporate risks aside, these days everything from your washing machine to your refrigerator to your cable box and home alarm may be networked and vulnerable to an attack. And while some “connected” devices are more secure than others, security researchers point out that it only takes a vulnerability in one of them to potentially compromise anything connected to your home network.
In the story above by #NewsMom KPIX Consumer Reporter Julie Watts, Jeremey Gillula of the Electronic Frontier Foundation warns that most connected devices are not designed for regular software and security updates. So, when a vulnerability is detected, there is no easy way to update the software.
In fact, of the nine name-brand baby monitors tested by Rapid7, only Philips released a software update to fix the security flaw.
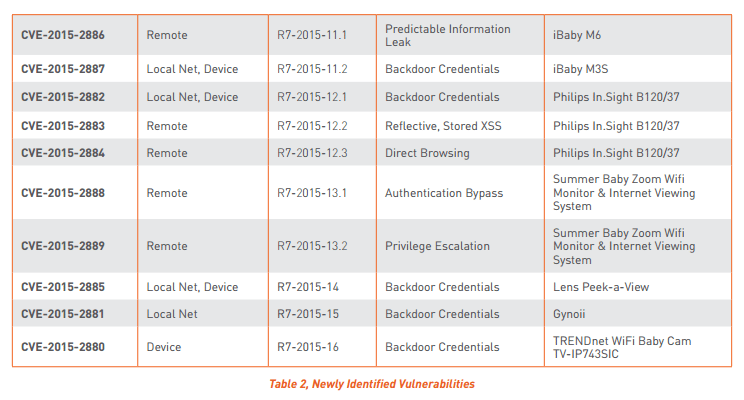
Rapid7 tested nine baby monitors, made by eight different companies, ranging in price from $55 to $260. Each received a D or F rating based on security flaws.
So what are your options?
Well, until now, “experts” simply encouraged people to set a secure password on their baby monitors. They believed most hackers were accessing the monitors by using the default password (published in the manual) that most people never changed.
But the Rapid7 researchers were able to hack into some of the baby monitors (above) in spite of secure passwords. Other monitors tested didn’t allow users to change the password at all.
Researches now suggest checking for software updates regularly (if your device allows for software updates) or simply unplugging your monitor when it’s not in use.
Keep in mind, you can opt for a monitor that is not connected to your Wi-Fi. However, those are not foolproof either. While non-“connected” monitors will prevent hackers from getting into your network and/or spying on your kid, Gillula points out that the local signal those monitors send out can still be intercepted.
So theoretically, someone could stand outside your home with a baby monitor receiver and try to pick up the signal coming from inside your house.
Though, unless someone is targeting you, that’s a far less likely scenario.

Leave a Reply